
19/10/2016
18:53

TG Soft' s C.R.A.M. has identified a new cryptomalware "Anubis". This new crypto-malware, when is executed, encrypts all files in the computer and rename them by adding the .coded extension. To descryt file, it is needed to send an email to get the key and the program to decode the files. |
INDEX==> Anubis how it manifests...==> The ransom demandend by Anubis ==> How to protect yourself from Anubis ==> What to do to mitigate the damage from Anubis |
|
Anubis, when is running on the pc , creates a computer's identified that will be send to the server C&C 190.14.37.117 togheter with usename and the pc's name with a POST request to the following page:
http://190.14.37.177/rs/createkey.php
| Form item: "idnumber" = "jPhHt30nkKhGBBYKzo1d" Form item: "username" = "XXXXXX" Form item: "pcname" = "XXXXXX-PC" |
The response contains the key RSA that will be used by the Malware to decrypt the key AES.
After Anubis will send a POST request to the following page:
http://190.14.37.177/rs/savekey.php
|
Form item: "idnumber" = "jPhHt30nkKhGBBYKzo1d" |
Where the information about a idnumber, pcname and aesencrypted are sent.
Anubis encrypts files with extensions such as those shown in the table below, and rename them by adding to the original name .coded esxtension.
|
.3dm, .3ds, .3g2, .3gp, .602, .aes, .arc, .asc, .asf, .asm, .asp, .avi, .bak, .bat, .bmp, .brd, .cgm, .cmd, .cpp, .crt, .csr, .csv, .dbf, .dch, .dif, .dip, .djv .djvu, .doc .docb .docm .docx, .dot .dotm, .dwg .dotx, .exe, .fla, .flv, .frm, .gif, .gpg, .hwp, .ibd, .iso, .jar .java .jpeg, .jpg, .key, .lay .lay6, .ldf, .lnk, .log, .m3u, .m4u, .max, .mdb, .mdf, .mid, .mkv, .mov, .mp3, .mp4, .mpeg, .mpg .ms11, .myd, .myi, .nef, .odb, .odg, .odp, .ods, .odt, .otg, .otp, .ots, .ott, .p12, .paq, .pas, .pdf, .pem, .php, .png, .pot .potm .potx .ppam, .pps .ppsm .ppsx, .ppt .pptm .pptx, .psd, .rar, .raw, .rtf, .sch .sldm .sldx, .slk, .stc, .std, .sti, .stw, .svg, .swf, .sxc, .sxd, .sxi, .sxm, .sxw, .sql .sqlitedb, .tar, .tbk, .tgz, .tif .tiff, .txt, .uop, .uot, .vbs, .vdi, .vmdk, .vmx, .vob, .wav, .wb2, .wk1, .wks, .wma, .wmv, .xlc, .xlm, .xls .xlsb .xlsm .xlsx, .xlt .xltm .xltx, .xlw, .zip, .7z |
Anubis, at the end of encryption, generates in the Desktop a file "Decryption Instructions"(without extension) with instructions for the payment of redemption:
|
IMPORTANT INFORMATION! |
And downloads an image(below) "ransom.jpg" in the user's folder:

Clicca per ingrandire l'immagine
Files that are encrypted by Anubis to be dencrypted require a payment of in BitCoin.
To obtain the information about the payment of the ransom you need to send an email as indicated in the image.
When the Alert screen on the side appears means that the Vir.IT eXplorer Pro's Anti-CryptoMalware integrated protection is acting and so, avoiding getting caught by the "panic" NOT close the window and perform the steps that are indicated:
|
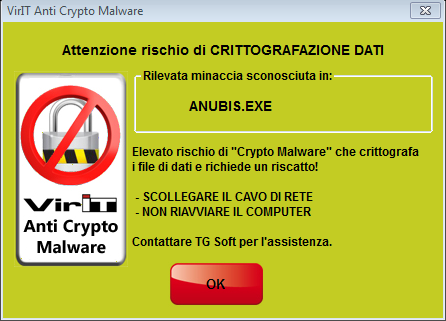 Clicca per ingrandire l'immagine 99,63% Average percentage Expectation of protected files from encryption thanks to Vir.IT eXplore PRO's Anti-CryptoMalware protection ==> Check the information |
With the Anti-Crypto Malware protection integrated in VirIT, the number of encrypted files by Anubis will be at most a few dozen.
The "sacrificed" files during the mitigation must be replaced with a backup copy, currently there aren't tools for recovering files .coded.
In the analyzed cases by the TG Soft's C.R.A.M., it was possible to recover files by using the shadow copies of the days preceding the attack.
If you opened an infected attachment and has been started the encryption, you could:
you have Vir.IT eXplorer Pro installed, correctly set up, up-to-date and running on your pc - in this case, you must follow the instructions on the Alert message and you will manage to save AT LEAST 99.63% of your data;
you have a AntiVirus software that DOESN'T DETECT, signal and halt the ongoing encryption - in this case you still could do
UNPLUG EVERY NETWORK CABLE
LEAVE YOUR COMPUTER TURNED OFF - every time the computer is rebooted and the malware is still active, a new encryption key will be used and the amount of money demanded as ransom will increase (note that paying the ransom does not guarantee the decryption and is therefore highlynot recommended)
Either way, remain calm and do not panic.
TG Soft
Anti-Malware Research Center