
01/03/2016
17:29

| After a few weeks from its first appearance, CryptoLocky is back thanks to a new wave of infected emails containing its dropper. CryptoLocky encrypts data files using .locky extension and demands 3 BTC as ransom. TG Soft's Anti-Malware Research Centre (C.R.A.M.) has acknowledged 2 types of emails containing CryptoLocky's dropper. |
INDEX=> Infected email: 1st type and 2nd type => The ransom demanded by CryptoLocky=> How to stay safe from CryptoLocky => How to contain CryptoLocky encryption damage |
|
In this case, these fake emails come from an unknown sender and their subject is "Delay with Your Order #<number>, Invoice #<number>":
Delay with Your Order #1629ADCD, Invoice #44196947 |
Click to show the picture fullscreen |
| The body of the email is the following: Dear Valued Customer,
The size of this .js file is about 5 KB (depending on the dropper) |
|
|
In this case, emails come from "documents@<receiver's domail>" and their subject is "Emailing: MX62EDO 01.03.2016".
|
Click to show the picture fullscreen |
| The body of the email is the following: Your message is ready to be sent with the following file or link attachments: MX62EDO 01.03.2016 SERVICE SHEET Note: To protect against computer viruses, e-mail programs may prevent sending or receiving certain types of file attachments. Check your e-mail security settings to determine how attachments are handled. --- This email has been checked for viruses by Avast antivirus software. https://www.avast.com/antivirus
The size of this .js file is about 5 KB (depending on the dropper) |
|
| .m4u .m3u .mid .wma .flv .3g2 .mkv .3gp .mp4 .mov .avi .asf .mpeg .vob .mpg .wmv .fla .swf .wav .mp3 .qcow2 .vdi .vmdk .vmx .gpg .aes .ARC .PAQ .tar .bz2 .tbk .bak .tar .tgz .gz .7z .rar .zip .djv .djvu .svg .bmp .png .gif .raw .cgm .jpeg .jpg .tif .tiff .NEF .psd .cmd .bat .sh .class .jar .java .rb .asp .cs .brd .sch .dch .dip .pl .vbs .vb .js .h .asm .pas .cpp .c .php .ldf .mdf .ibd .MYI .MYD .frm .odb .dbf .db .mdb .sql .SQLITEDB .SQLITE3 .011 .010 .009 .008 .007 .006 .005 .004 .003 .002 .001 .pst .onetoc2 .asc .lay6 .lay .ms11(Security copy) .ms11 .sldm .sldx .ppsm .ppsx .ppam .docb .mml .sxm .otg .odg .uop .potx .potm .pptx .pptm .std .sxd .pot .pps .sti .sxi .otp .odp .wb2 .123 .wks .wk1 .xltx .xltm .xlsx .xlsm .xlsb .slk .xlw .xlt .xlm .xlc .dif .stc .sxc .ots .ods .hwp .602 .dotm .dotx .docm .docx .DOT .3dm .max .3ds .xml .txt .CSV .uot .RTF .pdf .XLS .PPT .stw .sxw .ott .odt .DOC .pem .p12 .csr .crt .key wallet.dat |
| !!! IMPORTANT INFORMATION !!!! All your files are encrypted with RSA-2048 and AER-128 ciphers. More information about the RSA and AES can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem) http://en.wikipedia.org/wiki/Advanced_Encryption_Standard Decrypting of your file is only possible with the private key and decrypt program, which is on our secret server. To receive your private key follow one of the links: 1. http://i3ezlvkoi7fwyood.tor2web.org/EF423B59EA8A7266 2. http://i3ezlvkoi7fwyood.onion.to/EF423B59EA8A7266 3. http://i3ezlvkoi7fwyood.onion.cab/EF423B59EA8A7266 If all of this addresses are not available, follow these steps: 1. Download and install Tor Browser: https://www.torproject.org/download/download-easy.html 2. After a successful installation, run the browser and wait for initialization. 3. Type in the address bar: i3ezlvkoi7fwyood.onion/EF423B59EA8A7266 4. Follow the instructions on the site. !!! Your personal identification ID: EF423B59EA8A7266 !!! |
The desktop background image is changed into _Locky_recover_instructions.bmp:
The following Registry Key is generated:
HKEY_CURRENT_USER\Software\Locky:
[id] = victim's ID
[pubkey] = RSA public key
[paytext] = ransom information
[completed] = if the value is 1 then encryption has ended
Once CryptoLocky has encrypted the whole disk, it edits the "pending rename file" Registry Key to delete itself at the next reboot, leaving just the instruction for the ransom.
Come segnalato per gli altri Crypto-Malware è opportuno, appena ci si accorge della crittografazione dei dati in atto, procedere a:
| With the release 8.1.13 (18/02/2016) the heuristic-behavioural automaton included in Vir.IT eXplorer PRO has been updated in order to stop CryptoLocky attacks in its initial stages - other cryptomalware families, such as CryptoLocker, CTB-Locker, CryptoWall, CryptoEncoder, VaultCrypt, Crypto.FF, can still be halted. |  |
| On Windows 8, 8.1 and 10 machines, simply turning the computer off and the on again does not allow a correct update of Vir.IT eXplorer PRO's engine - this applies to every software update. | 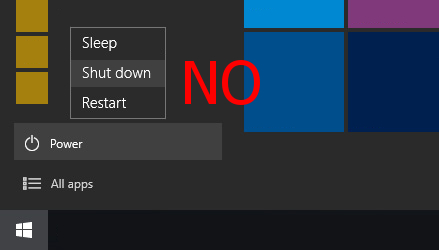 |
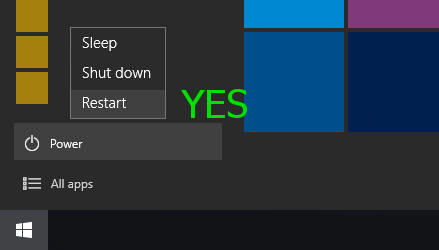
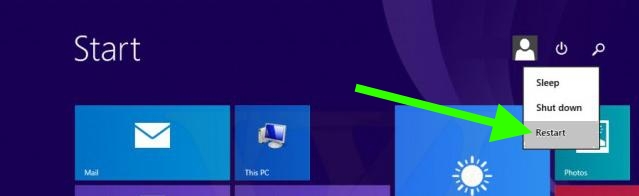
On Windows 10, you must follow these steps to correctly apply the updates:
|
 |
| Vir.IT BackUp is a technology built into Vir.IT eXplorer PRO and it is devised to guarantee a great degree of protection to its backup copies, even from new generation cryptomalwares. |