On 31th March we have analyzed the behavior at low-level of Petya Ransomware, whose analysis can be read from the news: "
Petya Ransomware X-Rayed !!!".
Now we can see how to determine the key used for cipher the Master File Table.
|
We have seen that the length of entered key must be between 16 and 73 characters. Only the characters between the space ' ' asc (0x20) and the '~' asc (0x7e) will be printed on the screen.
But from the entered key are taken the first 16 characters that belong to the following set:
123456789abcdefghijkmnopqrstuvwxABCDEFGHJKLMNPQRSTUVWX
|
|
this new key will be called 16 bytes Key: B0, B1, B2, B3, B4, B5, B6, B7, B8, B9, B10, B11, B12, B13, B14, B15
From the 16-byte Key you get a 32 bytes Key as shown in the figure:
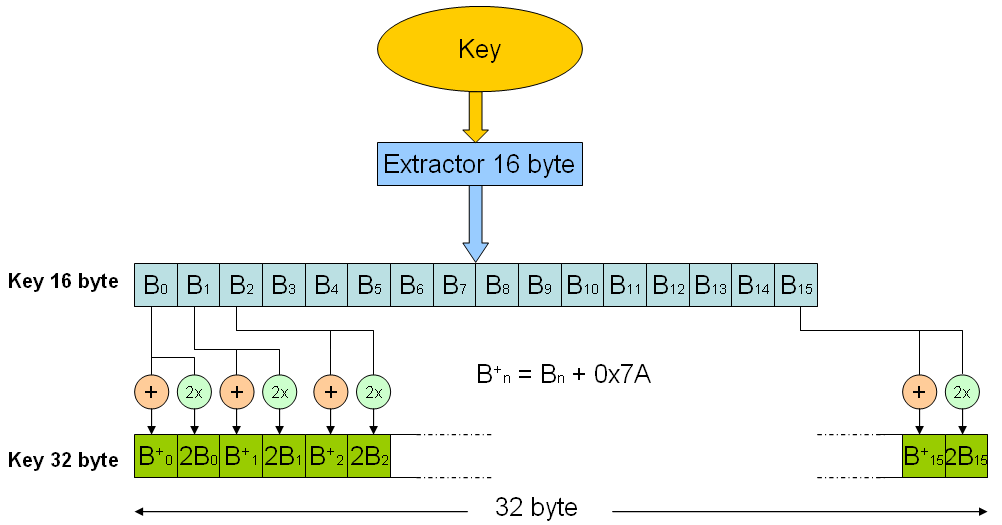
The 32-byte Key is used by Petya to decrypt.
Petya uses a hybrid version of "Salsa20". It creates a table, that we called "master table" of dimension 0x40 byte, where it initializes with following values:
- "expand 32-byte k"
- 32 byte Key
- 8 byte Vector of sector 0x36
- 8 byte with value 0
as shown in the figure:
From the "Master Table" of 0x40 byte Petya creates 2 equal tables (or vectors) of 0x20 byte: Tab_1 and Tab_2.
Tab_1 and Tab_2 are obtained taking the low word any 16 DWORD from the "Master Table".
In this way Petya will use only the bytes K0, K1, K4, K5, ..., K28, K29 of Key 32 byte.
The Tab_1 will be "shuffled" by algorithm Salsa and it summed (16 bit) with the Tab_2, in this way Petya will obtain a table of 16 DWORD with the XOR key to cipher (Tab_3).
In this way Petya uses only 8 on 16 Byte entered for the initial key, this will permit to obtain a way more easy the key used to cipher the MFT.
The bytes used by algorithm for cipher will be: B0, B2, B4, B6, B8, B10, B12, B14
So we can pass from an entered key of 16 byte to a 8 byte key, reducing considerably the number of possible combinations (548).
With the help of techniques as "Brute Force" or genetic algorithms will be possible to determine the key inserted and decrypt the Master File Table.
Update 11 april 2016: The researcher Leo Stone has realized a decoder of Petya: https://petya-pay-no-ransom.herokuapp.com/
Update 12 april 2016: With the upgrade
8.1.50 of VirIT (version LITE and PRO) we have released a new version of module called "Ninjavir", which permits to calculate the key used for cipher by Petya.
It's need connect the disk infected by Petya as secondary in an other pc and to install the version LITE (free) or PRO of VirIT.
You can download the Lite version from the page of
download.
After that you have installed VirIT and updated at version 8.1.50 (after the update please reboot your pc).
Open a Command Prompt window with administrator privilige.
Type the command:
c:\vexplite\ninjavir.exe /gui
Will open the window of "Ninjavir", please wait some seconds for the inizialization.
Click on the menu "
Decoder->Petya Ransomware" and select the drive infected by "Petya Ransomware". Ninjavir will show a message box with the value of key used for cipher by Petya:
Author: Eng. Gianfranco Tonello
Torna ad inizio pagina

