
27/09/2013
12:46

From few weeks a new banker variant using stealth techniques in order to hide its presence is spreading through the network.
This new banker variant, classificated as Trojan.Win32.Banker.XD, hides its presence at registry level in order to be run immediately at Windows Startup and disables the restore system configuration.
The sample analyzed by the C.R.A.M. (Anti-Malware Research Center) team has been identified with the name of Trojan.Win32.banker.XD,
File property:
MD5: DFFAFE13BE9FEA16EB79E4EF1A3E0E13
Size: 96608 byte
Name: [random name].exe
Language: Cinese (Hong Kong - R.A.S.)
Original file name: Bloemfon.exe
Product: Forepoint seroderm
Society: CamStudio Open Source Dev Team
When the file infected with Trojan.Win32.Banker.XD is executed, it creates a hidden folder with system attributes:
C:\Programmi\Common Files\h65guhb0
Two files are created inside the directory:
dttezfca.exe (a copy of the infection with read only and hidden attributes)
00177fae.txt (it is removed immediately after its creation, no data are written inside the file)
Actions performed on the Windows register:
Creates the key
HKCU\Software\WinZip\Uuid
Reads the value of the key
HKLM\SOFTWARE\Microsoft NT\CurrentVersion\ProductId
Checks the presence of possible AntiVirus on computer, querying in sequence the following keys:
HKLM\SOFTWARE\Symantec
HKLM\SOFTWARE\Avira
HKLM\SOFTWARE\ESET
HKLM\SOFTWARE\ArcaBit
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\AVG_UI
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\AVP
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Bdagent
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Trendo Micro Titanium
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\avast
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\MSC
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\BullGuard
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Sophos AutoUpdate Monitor
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\SplDerAgent
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\APVXDWIN
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\emisisoft anti-malware
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ISTray
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\G Data AntiVirus Tray Application
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\G Data AntiVirus Tray
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ZoneAlarm
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Bkav
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\V3 Application
Reads the value of:
HKCU\Software \Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders\Startup
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\Startup
To be executed at Windows Startup the Trojan.Win32.Banker.XDadds the following registry keys:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run
[j8hjfuin] = \Windows\Explorer.exe
HKLM\Software\Microsoft\Windows\CurrentVersion\Run
[j8hjfuin] = \Windows\Explorer.exe
The string j8hjfuin pointing to \Windows\Explorer.exe doesn’t fire up the traditional Windows Explorer.exe instead it starts the Trojan.Win32.Banker.XD loading it from the position C:\Programmi\Common Files\h65guhb0\dttezftca.exe
When a read request (at user mode) of the Trojan.Win32.banker.XD registry key is made, the returned value is the path of the following file "\Windows\Explorer.exe" instead of the Trojan.Win32.Banker.XD. original path.
The infection also goes to disable the Windows System Restore utility, blocking the execution of the original Windows file rstrui.exe.
To achieve this, the Trojan.Win32.Banker.XD adds the following registry key:
HKLM\Software\Microsoft\Windows NT\CurrentVersion\IamgeFileExecutionOptions\rstrui.exe
[Debugger] = <random name>_.exe
With this alteration, all started programs, with name rstrui.exe , are executed with the debugger set in the above registry key.
If the set debugger is not present in the system, this will generate an error execution of the required program.
In this case, the Trojan.Win32.Banker.XD, sets as default debugger a .EXE file with random name, changed at every computer restart, here some example:
txklyboa_.exe
lgzo_.exe
t_.exe
[nome casuale]_.exe
The specified debugger file it is not stored on the infected system.
With this technique the user will never use the Windows System Restore utility.
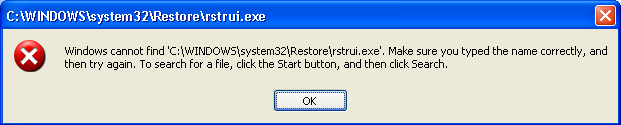
With this latest change the banker ensures a constant presence on the compromised computer blocking the possibility to restore the operating system to a prior point of infection.
The Trojan.Win32.Banker.XD makes connections to the http://www.romeoxx.xx (217.23.xxx.xxx) website on port 80, sending the following request:
POST /batman/ice/order.php HTTP/1.1 uploading five different values:
|
ps0= |
0000000000000000000000000000000000000 |
|
ps1= |
855BB5FD28AB63A326466800ED74AC5FF9325F43F |
|
cs1= |
5ECC83EA41CCE9EA6FCCD6EA7ACCCBEA7CCCD4E |
|
cs2= |
74CCDCEA65CCC9EA71CCD6EA6FCCDCEA33CCD |
|
cs3= |
5ECCEBEA5CCCF4EA45CCE9EA2ACC8CEA2BCC8F |
The Trojan.Win32.Banker.XD is detected and removed from Vir.IT eXplorer version 7.5.1.
---------------------------------
C.R.A.M. (Anti-Malware Research Center) team of TGSoft
The necessary cookies help make the website usable by enabling basic functions such as page navigation. The website cannot function properly without these cookies.
Cookie necessary to make certain specific contents usable such as: access to protected areas of the site, sending requests or subscribing to newsletters. The specific features of these sections will not be usable without this cookie.